Identity-driven detection and response for production environments
While others defend your inbox, we defend what makes you money
.svg)
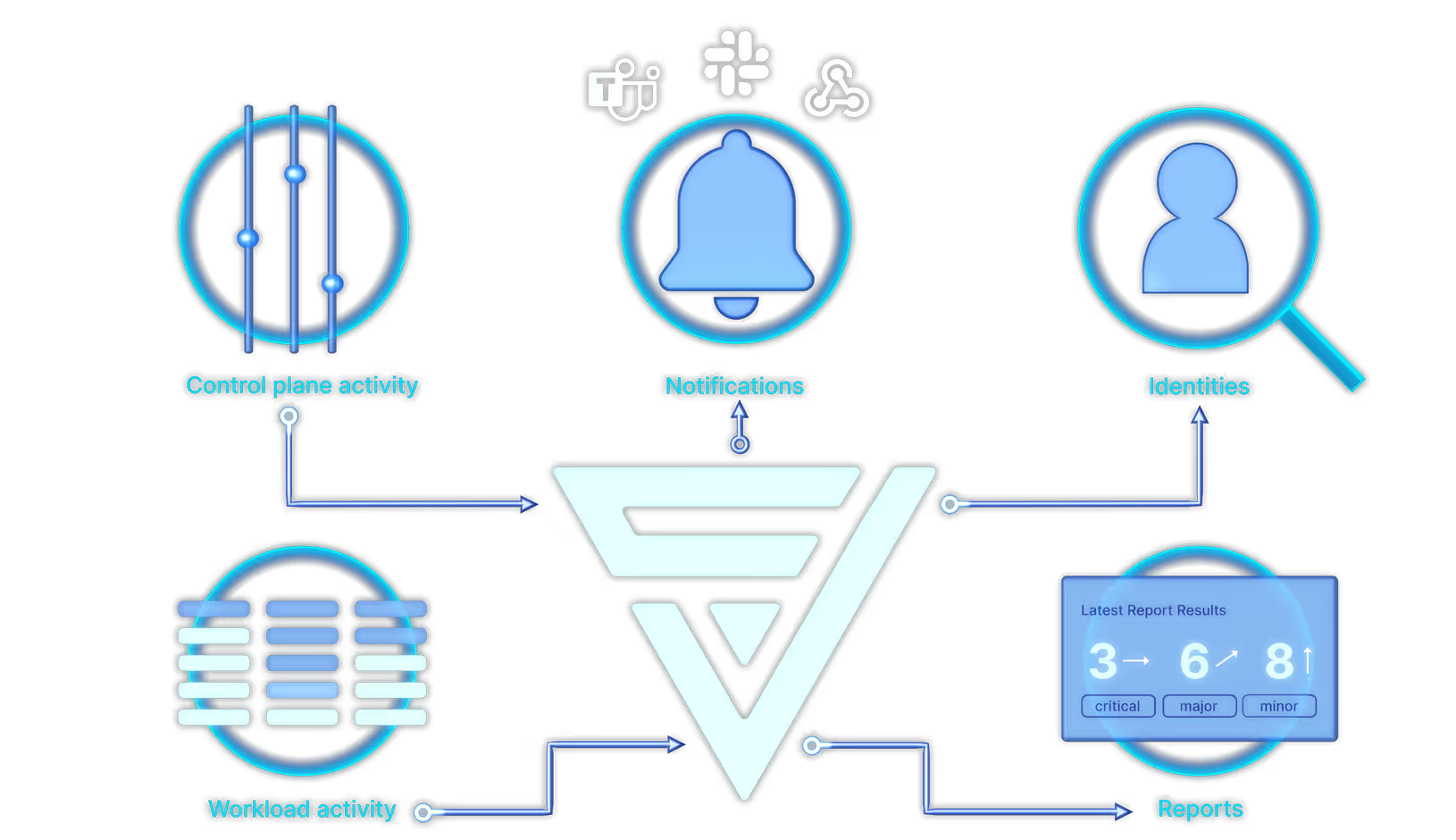
Identity attribution and detection
ClearVector discovers and maps all activity to human, non-human, and third-party identities across your entire production environment - from the control plane to containers to serverless functions. Within 30 seconds to 2 minutes, you know exactly who did what, eliminating hours-long investigations.
Built-in isolation to stop the adversary
When risky activity is detected, ClearVector enables instant isolation of compromised identities, S3 buckets, Lambda functions, and other resources with a single click - without breaking your production environment. This surgical precision stops attacks in progress while you investigate, with easy rollback once verified.
Unified visibility across all layers
ClearVector provides a single timeline that threads together activity from GitHub, through CI/CD pipelines, to AWS or GCP control plane actions, and into runtime behavior inside EC2, Lambda, and containers. This unified view reveals the adversary in ways that traditional tools miss.
Join companies that trust ClearVector
















Solutions
Built for your team
For detection and response teams (DART, CIRT, SIRT)
Stop chasing alerts across disconnected tools - ClearVector's identity-driven approach instantly answers "who did it" and provides one-click containment, transforming hours of investigation into minutes.

For security leadership
Demonstrate measurable risk reduction with the ability to stop the adversary, while your team focuses on strategic initiatives instead of manual log correlation.
Blog
Production insights, tips & news
Get started


%201%20(1).avif)
%201%20(3).avif)
%201%20(2).avif)


%201%20(4).avif)