Introducing realtime detection, isolation, and breach readiness
Today, we're excited to publicly announce two features for our identity-driven platform. First, our realtime detection and isolation feature, and second, our breach readiness feature.

Today, we're excited to publicly announce two features for our identity-driven platform. First, our realtime detection and isolation feature, and second, our breach readiness feature.
Introducing realtime detection and isolation
We launched ClearVector with the idea of making the job of the adversary extremely difficult. That's why we're on a mission to enable realtime intelligence and control over the identities operating in an environment. In addition, simply notifying you isn't enough; you need to prevent the adversary in realtime, prior to the exploitation of a vulnerability. With this in mind, we designed not only the ability to identify risky activity, but also stop the identity performing the activity in its tracks.
Today, we're excited to publicly announce our realtime detection and isolation feature. This feature helps you identify and stop risky activity. We leverage our purpose-built risk engine and our identity engine to, in realtime, discover new identities, map all activity to identities, and determine the risk of the activity over time and in realtime. We notify you of risky activity in app, or in your workflow - such as Teams or Slack. Below, you see a Slack message showing 'alice' and 'bob' backdooring a few accounts using an open-source exploitation framework, followed by a 'trent' and 'eve' disabling key security controls. A single-click from the ClearVector console lets you isolate the identities.
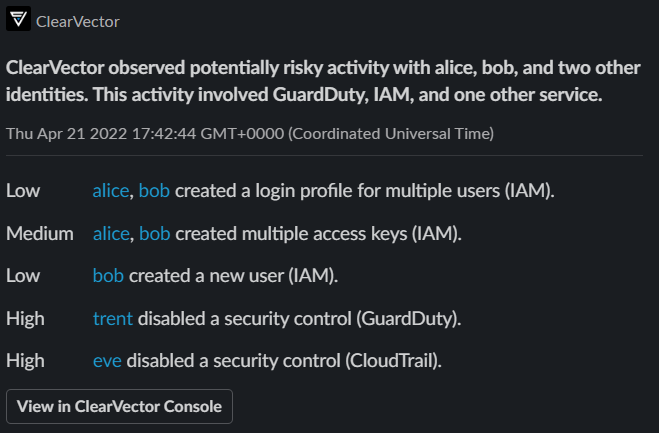
Another of our core philosophies is making things simple and approachable. You shouldn't need to know what question to ask or be a cloud expert to stay safe in the cloud. In the above scenario, you'll notice natural language is used to communicate what happened. In a future blog post, we'll expand on our approach and our multiple layers of natural language abstraction.
Stay tuned for future blog posts about adversary activity we've observed in compromised environments.
Introducing breach readiness
ClearVector also holds a core belief that adversaries can and will compromise anything if they are motivated to do so. What we've termed "breach readiness" has two major components: first, tackling and monitoring the items that reduce your risk the most, and second, figuring out what happened if risks are realized (to understand why and prevent them from happening again).
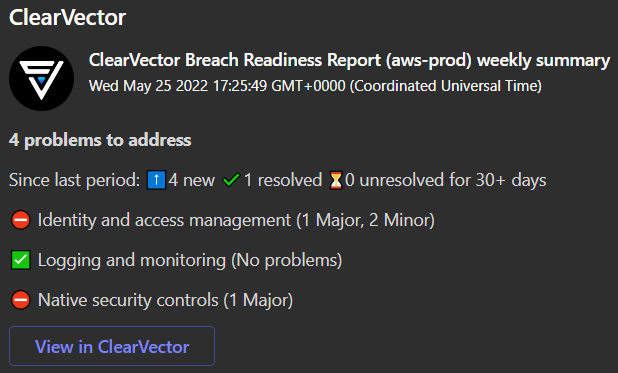
For the first component, think of this as the airbags and seatbelts in your car. Although there are many other things to think about when driving from point A to point B, there are a small set of things that materially contribute to crashes, or significantly reduce your chances of a major injury in a crash. As part of our realtime breach readiness capabilities, we're releasing our breach readiness report. This report focuses on the top risks that materially impact the security of your environment. The report does two things: 1) Focuses you on the most important items to materially reduce risk. We believe these are the bare minimum to operate safely in the cloud (i.e., the equivalent of a "safety inspection" in the auto world), and 2) Notifies you in realtime if these change. With our identity driven approach, we also tell you who made this change, not simply that a change happened "since the last scan".
Below, you see a Teams message detailing both scheduled and realtime reporting of a few major items we believe are key to operating safely in the cloud.
For the second component, in the event of a breach or risk being realized, you need the ability to "go back in time" and have a "digital flight recorder". In our experience, this is non-trivial to do properly, and is one of the biggest gaps when responding to a breach and trying to understand the "who", "why", and "how".
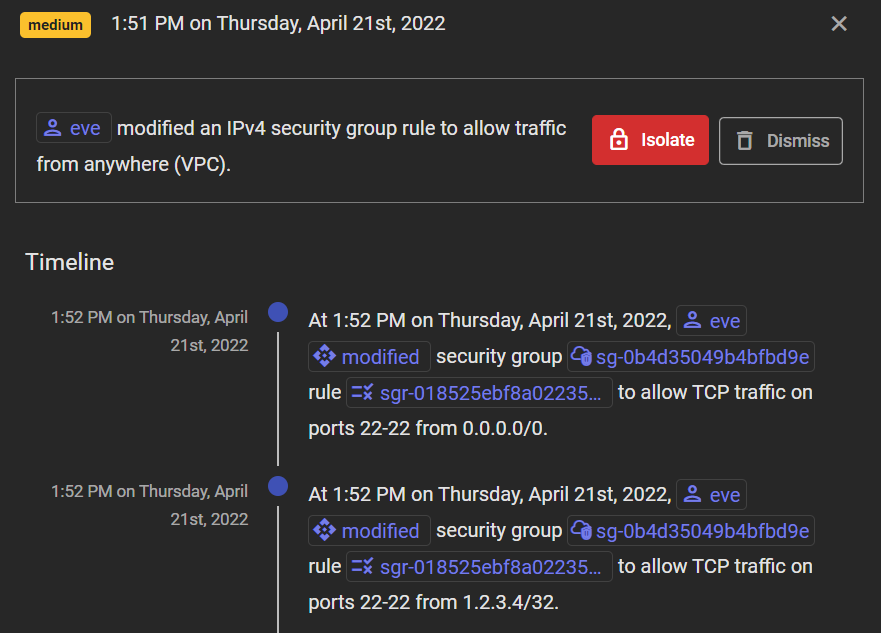
Typically, the first question is, "What logs do you have?" We've been there, and created a purpose-built, realtime, identity-driven "CloudDVRTM" to solve this problem. In addition, our CloudDVRTM sits outside your environment, further insulating you from adversaries that delete data within your environment.
For example, below you can easily get a sense for what "eve" is doing around the time of the risky activity:
Future blog posts will dive deeper into our realtime, identity-driven CloudDVRTM.
Existing ClearVector customers already have access to these features. Current customers will automatically see the new reporting features in the app, and in Slack and Teams.
Stay tuned for further in-depth posts! We're just getting started. Check us out at fwd:cloudsec this year, schedule some time at AWS:reinforce, DM us on Twitter, or contact us directly to learn more.
